Data Confidentiality (Yours and Your Customers)
While we also have an extensive legal mumbo-jumbo Privacy Policy - the bottom line is this:
Our revenue consist of only one thing - our service to you. We DO NOT ever try to make additional money off of the data either you or your customers provide while using the service. We NEVER rent, sell, loan, give away or distribute any such data unless required by law enforcement. Your and your customers data is confidential - PERIOD!
Data Security
Since the Vcheck servers do not handle any type of credit card data, we are not required to be PCI compliant. However, we maintain our servers as though we are. In the 15+ years Vcheck has been server-based, we have never had an outside security breach.
Secure Connections
All connections to and from the Vcheck system are AES 256-bit encrypted via SSL. That means data between a browser and the server is secure.
Hardware and Software Firewalls
The Vcheck system runs on a secure cloud server at one of Amazon Web Services data centers. They provide hardware firewalls to prevent the most common types of attacks. Additionally, the server itself runs on Apache and uses it's built-in firewall. We also have code in place to thwart brute force login attempts.
Database Encryption
All the system databases are heavily hashed/encrypted and can only be decrypted by the system source code. There is never any sensitive data left unencrypted.
Source Code Encryption
As stated above, the database can only be decrypted via keys and code in the Vcheck source code. The system source code is also encrypted with Ioncube and will only run on the system server.
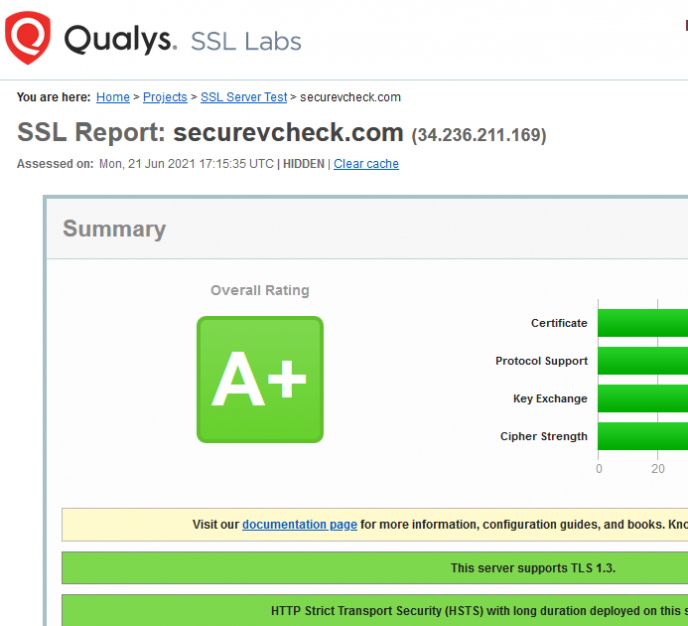
Periodic Security Scans
We have the Vcheck servers periodically scanned for security by Qualys SSL Labs - a leader in server security. Although no server is 100% bullet proof - we do a pretty good job. You can download a sample of a recent scan by clicking on the screenshot below. You may also run a current report yourself here.
In addition to the basic Qualys scan, we also use the world's most widely used web app scanner (OWASP ZAP) to run scans for the following:
- Vulnerability Assessment – The system is scanned and analyzed for security issues.
- Penetration Testing – The system undergoes analysis and attack from simulated malicious attackers.
- Runtime Testing – The system undergoes analysis and security testing from an end-user.
- Code Review – The system code undergoes a detailed review and analysis looking specifically for security vulnerabilities.
Data Security and Confidentiality Agreement
Some of our merchants are in heavy regulated industries that require specific written data security agreements in order to remain industry compliant. We have a extensive agreement we use in such cases.